Products

As the Web3 ecosystem evolves, so do the security challenges that protocols and companies face. Web3 Threat Intelligence plays a crucial role in understanding the motives and behaviors of blockchain hackers, enabling proactive security measures.
In this article, we will explore the essential elements that affect Web3 security, highlighting the importance of threat intelligence and real-time monitoring to strengthen defenses against cyber threats.
Web3, the next evolution of the internet, is built on blockchain technology and smart contracts. While it offers transparency, immutability, and decentralized control, its intricate architecture introduces vulnerabilities that malicious actors may exploit. Threat researchers play a vital role in uncovering and analyzing these vulnerabilities.

The decentralized nature of Web3 introduces novel challenges, including:
Effective threat intelligence could have prevented the recent Multichain & Curve attack by identifying and addressing Vyper programming language vulnerabilities, compromised private keys, and the increased activity of MEV bots in a proactive manner. Swift action through security patches, audits, and proper configuration management would have mitigated the impact and safeguarded user funds.
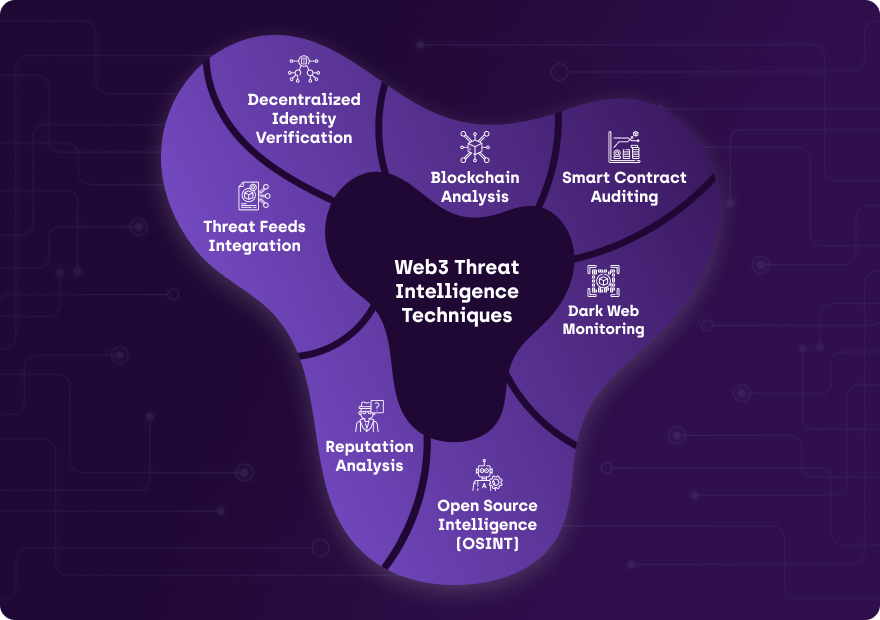
Threat researchers are cybersecurity experts dedicated to identifying potential risks, analyzing attack vectors, and staying one step ahead of cybercriminals. Through meticulous analysis of blockchain protocols, smart contracts, and decentralized applications (dApps), these researchers can discover and disclose vulnerabilities to protect the Web3 ecosystem.
Web3 Threat Intelligence is a powerful tool in combating the evolving landscape of cybersecurity threats in the decentralized world. By embracing real-time monitoring, proactive security, and adopting best practices, Web3 protocols and companies can safeguard their assets and protect users from potential attacks. Balancing different factors and understanding the tradeoffs will be key to building a secure and resilient Web3 ecosystem.
Identify patterns and anomalies across blockchains in real-time for proactive mitigation.
Book a Demo